01
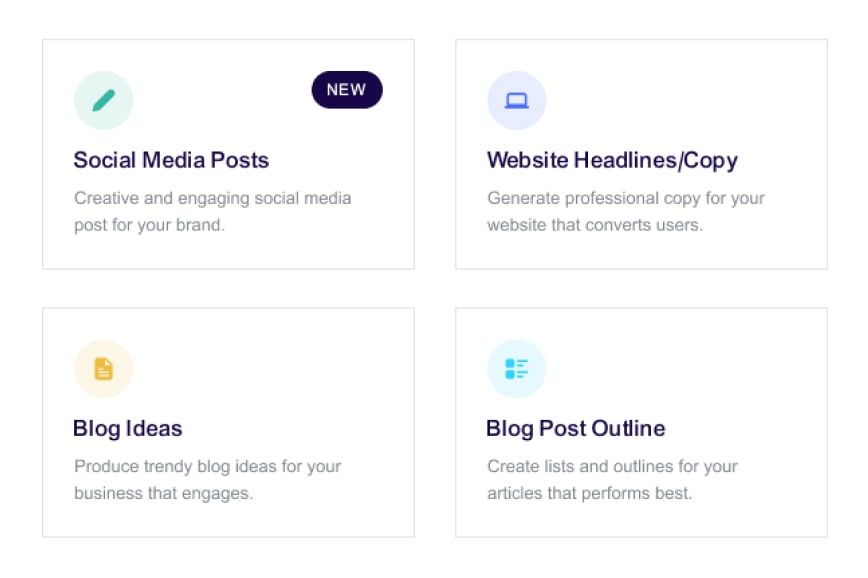
Asset Inventory
Resources, IAM policies, users and more are exported to an asset inventory. Data classification is used to determine risk.
Learn about the latest technology to secure cloud environments.

Resources, IAM policies, users and more are exported to an asset inventory. Data classification is used to determine risk.
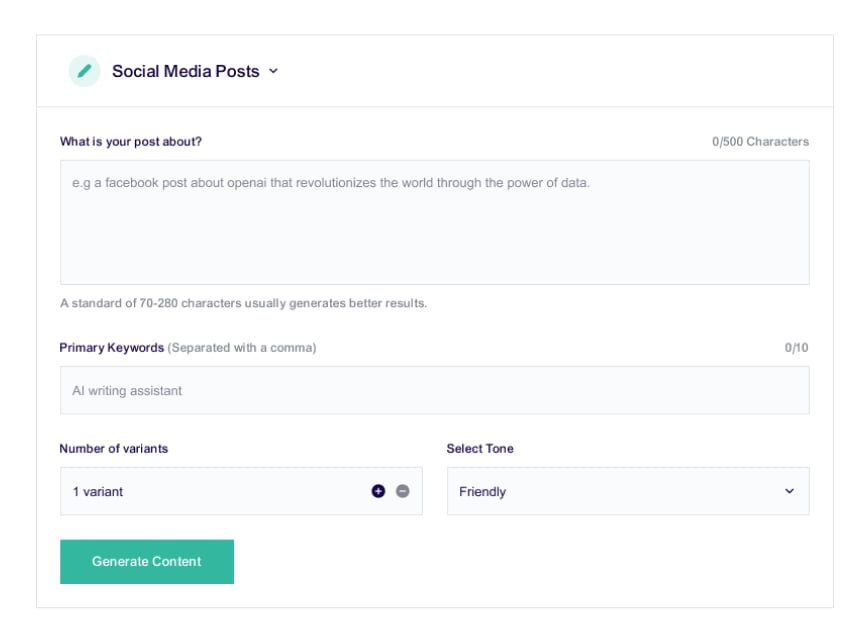
Our intelligent AI models will calculate attack paths and determine an associated risk score.
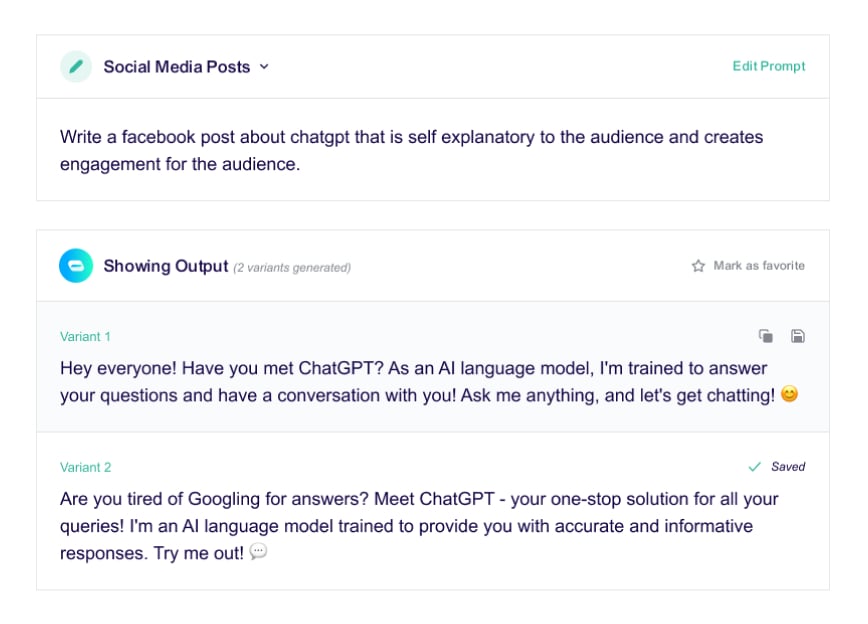
Gain insights in prioritization and remediation. Optionally alert the team responsible automatically.